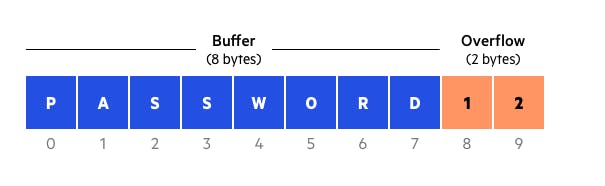
What is a Buffer?
A buffer is a portion of physical storage memory designated for the temporary storage of data during its transfer from one location to another. Typically, these buffers are situated in Random Access Memory (RAM) and serve the purpose of enhancing performance and enabling efficient data access. In the context of video streaming, for instance, the video player operates by downloading and temporarily storing approximately 20% of the video within a buffer before commencing the streaming process. This approach ensures that minor fluctuations in the connection speed or brief service interruptions do not significantly impact the quality and continuity of video streaming performance.
Buffer Overflow Attacks
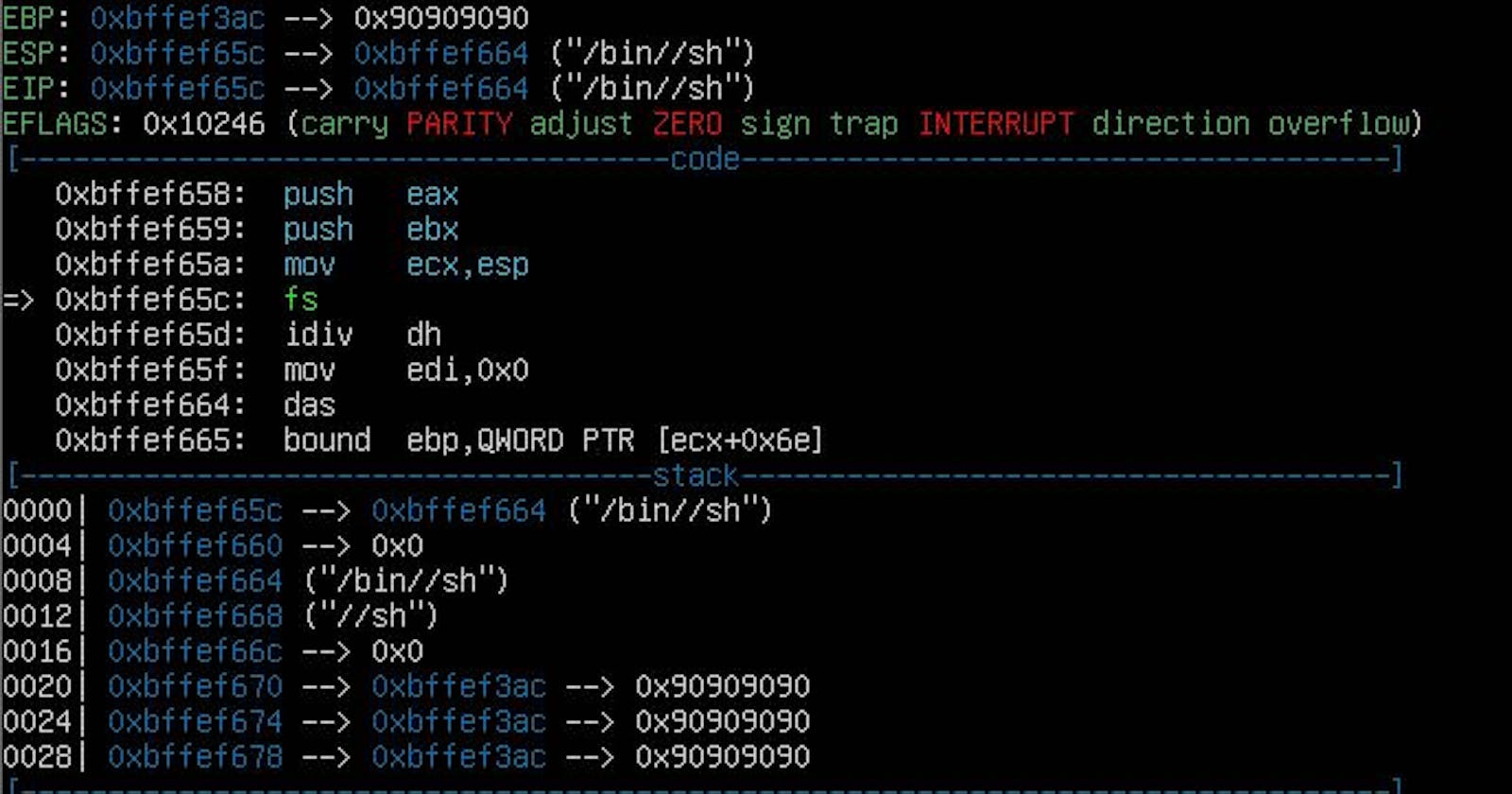
So what exactly are buffer overflow attacks and how do they work?
As the name suggests, a buffer overflow is a vulnerability that occurs when a program can write more data to a buffer, than it is designed to hold. The excess data overflows into the adjacent buffer, overwriting its contents and enabling the attacker to change the flow of the program and execute a code injection attack.
Let us consider some basic examples of this attack.
char buf[BUFSIZE];
gets(buf);
This code snippet is vulnerable to buffer overflow because it doesn't limit the size of input data read by gets(), allowing potential overflows and memory corruption if the input exceeds the buffer size.
char buf[64], in[MAX_SIZE];
printf("Enter buffer contents:\n");
read(0, in, MAX_SIZE-1);
printf("Bytes to copy:\n");
scanf("%d", &bytes);
memcpy(buf, in, bytes);
In this, the code relies on user input to control its behavior, but it adds a level of indirection with the use of the bounded memory copy function memcpy(). This function accepts a destination buffer, a source buffer, and the number of bytes to copy. In this case, memcpy(buf, in, bytes); is vulnerable to buffer overflow as it doesn't verify if 'bytes' exceeds the size of the 'buf' array, potentially leading to memory corruption if 'bytes' is greater than the available space in 'buf.'
Buffer overflows are one of the oldest and most common causes of arbitrary code execution vulnerabilities, and are very common in programming languages like C and C++, both of which have no built-in protection against accessing or overwriting data anywhere in memory. They do not automatically check if data written to a buffer is within the bounds of that buffer.
Types of Buffer Overflow Attacks
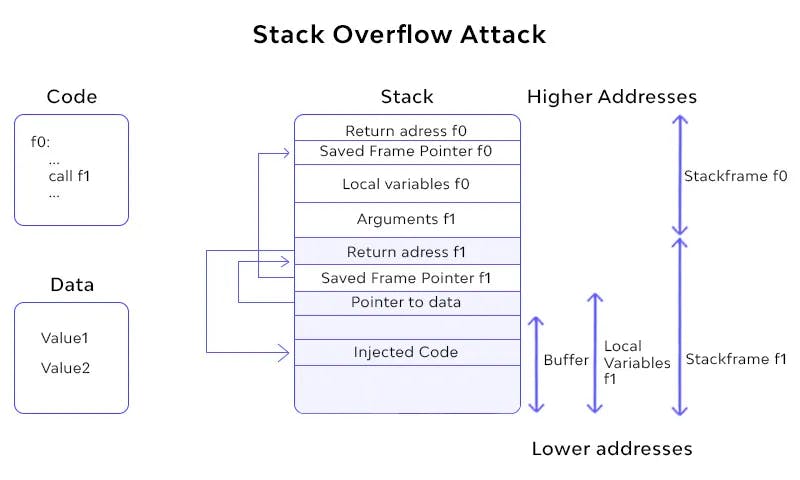
Stack-Based Buffer Overflows: The most common type of buffer overflow attack that occurs when an attacker injects data with malicious code into an application, which is then stored in a stack buffer. This overwriting action affects the stack's data, including its return pointer, ultimately granting control to the attacker.
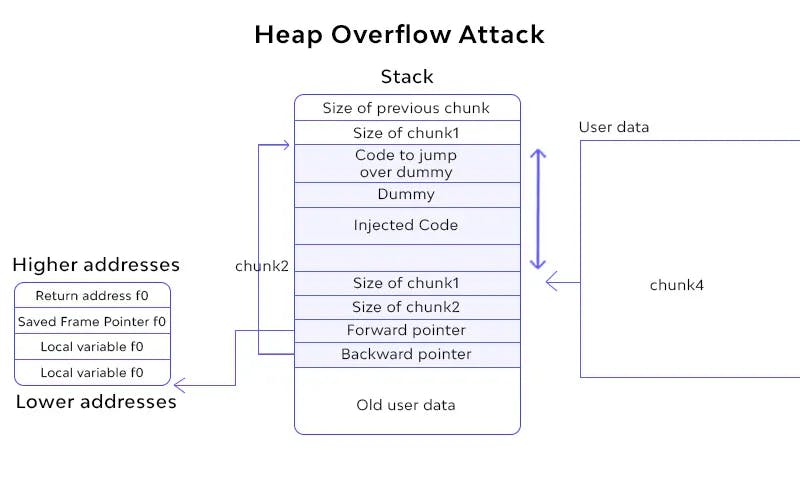
Heap-Based Buffer Overflows: The heap overflow occurs when a piece of memory is assigned to the heap and the data is written to that memory without the data being checked. This may result in some critical data structures in the heap, such as heap headers, or any heap-based data, such as dynamic object pointers, which can overwrite the virtual function table.
Format String Attack: Format string exploits are a type of vulnerability that arises when an application processes input data as a command without adequately validating it. This vulnerability enables malicious actors to execute arbitrary code, gain access to stack data, or induce segmentation faults within the application. Consequently, this can result in actions that compromise the security and reliability of the system.
Famous CyberAttacks caused due to Buffer Overflow
According to MITRE, buffer overflows account for over 10,000 of the known software vulnerabilities, 23% of which are considered severe.
Heartbleed
Heartbleed, a widely publicized security bug in OpenSSL that came to light in 2014. It exploited a buffer over-read vulnerability in the OpenSSL cryptography library used for the implementation of the Transport Layer Security (TLS) protocol. The root cause was the lack of bound checking. Experts estimated as much as two-thirds of https-enabled websites worldwide were affected leading to $500 million worth of damages.
WhatsApp VoIP
In May 2019, a security flaw affecting all WhatsApp products was disclosed. This vulnerability leveraged a buffer overflow in WhatsApp's VOIP stack on mobile devices, permitting remote code execution through a meticulously crafted sequence of SRTP (secure real-time transport protocol) packets sent to a designated phone number. The exploit was employed to compromise more than 1,400 smartphones by merely initiating a WhatsApp voice call, even if the call went unanswered.
Prevention of Buffer Overflow Attacks
Bounds checking: Implementing bounds checking within abstract data type libraries can effectively reduce the risk of buffer overflows. Usage of vulnerable standard library functions like gets(), strcpy(), and strcat() should be avoided.
Executable space protection: To enhance security, it is important to designate memory regions as non-executable. This prevents the execution of machine code within these regions.
Usage of modern operating systems: Modern operating systems come equipped with built-in runtime protection mechanisms. These features include randomized address space layout, which reorders the main data areas of a process, and safeguards against non-executable regions being exploited.